When you say SAP, many people have some familiarity, as SAP has been at the forefront of enterprise resource planning (ERP) technology since their inception. SAP was founded in 1972, and they’ve transformed more than S/4HANA. They’ve introduced new solutions to push organizations forward, such as SAP SuccessFactors, SAP Analytics Cloud, Business Technology Platform, Ariba and more. Organizations all over the world have adopted SAP cloud technology to scale their operations and run more efficiently. But what about the highly regulated industries who sought the innovation of SAP, but were restricted by government regulations and mandates within the cloud?
The solution: SAP National Security Services (SAP NS2). In 2005, we began our mission to give even the most highly regulated organizations the ability to adopt SAP technology. The creation of SAP NS2 was inspired by the need to have a proxy company, independent from SAP, that could provide government and defense agencies a secure pathway to the cloud.
Overcoming Obstacles: A finetuned, secured SAP cloud adoption process
I joined SAP NS2 in 2012, and I have seen firsthand how the synergy between SAP and SAP NS2 has revolutionized entire industries. While SAP NS2 is an independent subsidiary, we have created a working model that allows us to take SAP’s commercial innovation, incorporate the security aspects that we specialize in, and deploy solutions in our secure cloud environment.
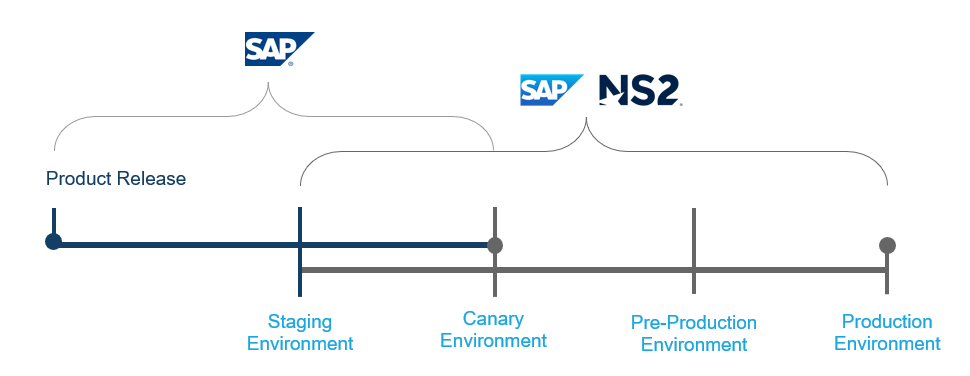
SAP works closely with each customer to understand their mission, and once a need for heightened security is identified, we step in to ensure our customers can have the best of both worlds: SAP innovation and the requisite government-attested security controls. With each SAP product release, SAP NS2 creates pre-prod and production environments to ensure it meets the needs of our customer base.
SAP innovation that adheres to NIST 800-53, ITAR, and FedRAMP® Moderate Controls
We take our time to ensure our customers are protected to the highest degree, and through our deep industry knowledge, our dedicated security team, and assessments conducted by third-party organizations (3PAO), our secure cloud offerings adhere to NIST 800-53, ITAR, and FedRAMP® Moderate Controls.
We also employ automation practices that mitigate vulnerabilities before it’s too late. The following regulatory requirements are included in our automation practices:
• Continuous Web Application Scanning
• Continuous Monitoring (ConMon)
• Centralized Intrusion Detection System
• Centralized Vulnerability Scanning
• Automated Security Patching
• Automated Hardening
• Potential updates due to global capabilities
• Strict Resource Requirements (e.g., clearances)
• Universal security model applied across multiple solutions
All About Alignment: The answer to organizations running at their best
We understand the immense value that SAP’s cloud technology can bring to our customer base, and we have made it our mission to provide regulated organizations the innovation of commercial SAP cloud solutions without compromising on security. By the time SAP solutions are deployed to our customers, they have been thoroughly vetted and secured. This close alignment and collaboration with SAP, customers, and partners is how we help customers run at their absolute best.









